Assume someone has access to your data
In a 2018 Thales Survey of 1200 companies, 71% of the US enterprises reported suffering at least one data breach. And 42% of those breached this year had been breached in the past.
More companies report data breaches each year as they continue to adopt digital transformation technologies ahead of their ability to secure them properly. The survey reveals that 94% of organizations with sensitive data use digital transformation technologies like IoT, big data and enterprise cloud which compounds the problem. Today, organizations have to assume a security posture where someone has access to their data and is ready to infect their systems with malware.
Most notorious malware: ransomware
Ransomware is a top variety of malicious software, found in 39% of the cases where malware was identified, according to a Verizon 2018 Data Breach Investigations Report. It encrypts or damages your files to demand ransom in return for your data.
Ransomware has become the malware of choice for cybercriminals as they are effective and easy to deploy. With off the shelf toolkits, any amateur can create and deploy ransomware in a matter of minutes. There is no need for them to figure out how to monetize the stolen data, nor is there a cost or risk involved.
As they became more widespread, ransomware attack models evolved beyond phishing emails. Ransomware like WannaCry have discovered new methods of entry; some of which require no user interaction. These evolved models make it easier to breach and harder to contain, leaving organizations exposed and always in a rush to quickly resolve or succumb to paying ransom.
The real killer not ransom - but downtime
Many organizations actually do consider paying ransom because they want to be able to access their files again as soon as possible. The real setback for them is downtime and the lost opportunity.
Besides the ransom paid, ransomware cost includes downtime, labor, device cost, network cost and lost opportunity. A 2017 Sophos Report, based on a survey of 2700 IT decision-makers, estimates this cost at $18.6 billion for U.S. businesses of 100 or more people in the last year.
This high downtime cost compels companies to look closely into their typical security response and to identify key challenges.
Your typical response - unscalable and cumbersome
Typical response to a basic ransomware attack
To start, let’s look at how an organization typically deals with a basic ransomware attack model like phishing.
The Verizon 2018 Report reveals that you have 16 minutes until the first click on a phishing campaign. The first report from a savvy user will arrive after 28 minutes.
After the first incident or report, the incident response team follows the playbook: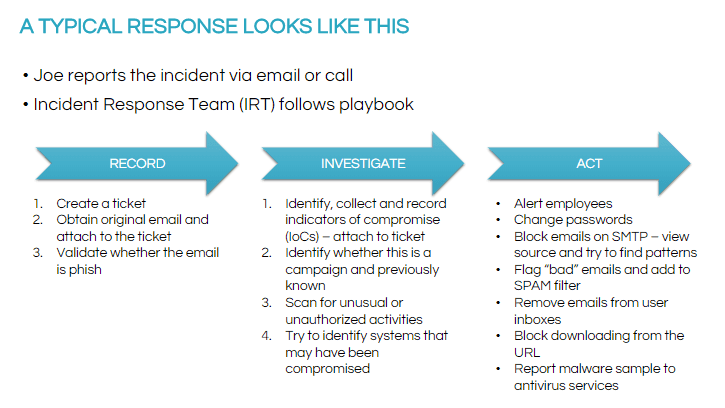
This process involves a lot of manual steps, making it unscalable and inefficient in preventing ransomware from spreading or from efficiently resolving it.
Typical response to vulnerabilities
For more advanced ransomware attack models, proactive teams research online and do their best to execute patches. Here is a typical workflow the vulnerability response team follows:
1. Notice
- For popular attacks, teams research online to uncover information about the exact vulnerabilities being exploited. These are typically by the Common Vulnerabilities and Exposures or CVE number released by NIST and the NVD.
- Specific patches are identified to remediate the vulnerabilities.
2. Investigate and Record
- Adhering to the change process, an emergency change request is created.
- The matching CVEs and any information about affected systems are exported from the vulnerability scanner, or at some organizations, multiple scanners.
3. Take Action
- The patch then needs to be tested in development and applied in production.
- Vulnerability response team needs to determine who the owners or patch teams of the affected systems are. Determining patch or remediation ownership can become problematic when emails and phone calls are used to communicate with stakeholders.
- Eventually rescans will need to occur to make sure all systems have been patched.
As is evident in the above workflow, there is no visibility across teams, making it hard to collaborate and patch vulnerabilities. Moreover, important details slip through cracks because emails and spreadsheets are used to manage the patching process.
This workflow, again, can’t scale. During an outbreak, the time it takes to gather information and communicate can result in ransomware continuing to spread.
Seamless collaboration needs to happen across teams and tools
To minimize the downtime and damage caused by ransomware, seamless collaboration has to be established between different teams and across different security tools. This collaboration between security and IT operations teams is termed SecOps. Introducing intelligent workflows and automation can further help organizations prioritize and resolve threats quickly based on impact.
How SecOps can help deliver an effective response for ransomware
SecOps provides your security team visibility across teams and security tools. To drive efficiency, the team can then automate for repeatable responses and close the loop by passing the information to vulnerability scanner or SIM, therefore reducing the organization’s risk to ransomware.
Effective response to Phishing
By leveraging SecOps, you can deliver automatic and effective responses to a ransomware infected email.
- The security team has the visibility to see which email domain is sending unwanted programs and which business services are being attacked the most.
- If they see several events where a firewall is being attacked from a certain IP range, they can put an automated workflow in place that sends a command over to the firewall to block that IP range.
- This way, every time this incident happens, the workflow takes care of it.
- If anyone was involved in this security incident, an automated survey is sent out to gather feedback on areas of improvement.
Effective response to vulnerabilities
WannaCry attackers were exploiting security vulnerabilities in Micsrosoft’s SMB. When notified, everyone was scrambling to apply a critical patch. With threat intelligence and automated workflows, this could have been managed better.
This is an instance of how SecOps can be leveraged to deliver an efficient vulnerability response in no time:
- The team has visibility into all their vulnerabilities which are prioritized based on potential business impact.
- Their vulnerability scanner notifies them of any critical patch that they are missing. With workflows in place, a change is automatically created and sent for approval.
- Once the change gets approved, it starts deployment with the endpoint management tool or notifies the IT team responsible to develop the patch.
- The team has real time visibility into the status and can schedule a report to be sent to the stakeholders.
- Next, a scan is automatically performed to ensure that the vulnerability is taken care of.
How you can win - Action plan
Hackers continue to outpace security teams with their evolved attack models. With the damage downtime does, you can’t afford a malware like ransomware. Now that you know how SecOps can help tackle these malware, here is your action plan:
Evaluate your typical response. Identify the problematic areas in your process such as cross department coordination, lack of asset and application visibility, and inability to track the vulnerability lifecycle.
- Start with the basic hygiene of your security.
- Does your team actively scan for vulnerabilities?
- If yes, do they execute both internal and external scans?
- Who in your organization has access to your sensitive data?
- Is your data physically secure?
- Create a common view combining vulnerability and IT configuration data using the same platform to lay the foundation for more advanced capabilities such as prioritization and routing to IT.
- Define end to end vulnerability response processes, then automate as much as much as possible. Make sure that you automate repeatable vulnerability response processes.
- Improve upon existing workflows, processes and integrations to meet your organization’s changing needs.
Does that sound like a lot of work?
INRY helps organizations win their fight against malware like ransomware. With our capability planning expertise, we work extensively with organizations to automate and orchestrate their security operations.
As a ServiceNow Elite partner, we leverage the NOW platform to drive efficiency for your security teams.
Feel free to reach out to us for a quick consultation with one of our security experts.